The Impact of IoT Applications on Our Daily Lives
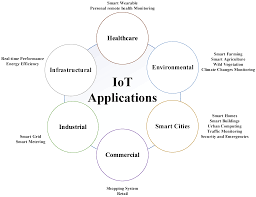
The Internet of Things (IoT) has revolutionised the way we interact with technology and the world around us. IoT applications have become an integral part of our daily lives, offering convenience, efficiency, and connectivity like never before.
One of the most common IoT applications is smart home technology. From smart thermostats that adjust the temperature based on your preferences to smart security systems that allow you to monitor your home from anywhere in the world, these devices have made our homes safer and more energy-efficient.
In healthcare, IoT applications have enabled remote patient monitoring, wearable health devices, and smart medical equipment that can transmit data in real-time to healthcare providers. This has improved patient care, reduced hospital readmission rates, and allowed individuals to take control of their health.
IoT applications have also transformed industries such as agriculture, manufacturing, transportation, and retail. Smart sensors can monitor crop conditions and automate irrigation systems in agriculture. In manufacturing, IoT-enabled machines can communicate with each other to optimise production processes. In transportation, connected vehicles can improve road safety and reduce traffic congestion.
As IoT technology continues to advance, we can expect even more innovative applications that will further enhance our daily lives. From smart cities that use data analytics to improve urban planning to wearable devices that track our fitness levels and provide personalised recommendations, the possibilities are endless.
In conclusion, IoT applications have had a profound impact on how we live, work, and interact with the world around us. As this technology continues to evolve, it is important for individuals and businesses to embrace these innovations and harness the full potential of IoT for a smarter and more connected future.
9 Essential Tips for Securing and Managing IoT Applications
- Ensure strong security measures are in place to protect IoT devices and data.
- Regularly update software and firmware to ensure IoT devices are running on the latest versions.
- Implement proper access control mechanisms to restrict unauthorized access to IoT systems.
- Use encryption techniques to secure communication between IoT devices and servers.
- Monitor IoT device performance and behaviour for any anomalies that may indicate security breaches.
- Consider the privacy implications of collecting and processing data from IoT devices.
- Ensure interoperability of different IoT devices by following industry standards and protocols.
- Provide user education on how to securely use and manage IoT devices in their environment.
- Have a disaster recovery plan in place to mitigate the impact of any potential IoT system failures.
Ensure strong security measures are in place to protect IoT devices and data.
It is crucial to implement robust security measures to safeguard IoT devices and data. With the increasing interconnectedness of devices in the Internet of Things ecosystem, ensuring strong security protocols is essential to prevent cyber threats and data breaches. By encrypting data, regularly updating software, using secure authentication methods, and monitoring network activity, individuals and organisations can mitigate risks and protect their IoT infrastructure from potential vulnerabilities. Prioritising security measures not only safeguards sensitive information but also ensures the reliability and integrity of IoT applications in our daily lives.
Regularly update software and firmware to ensure IoT devices are running on the latest versions.
It is crucial to regularly update the software and firmware of IoT devices to ensure they are operating on the latest versions. By keeping these updates current, users can benefit from improved security features, bug fixes, and enhanced performance. Regular updates also help to protect IoT devices from potential vulnerabilities and cyber threats, ensuring a safer and more reliable user experience.
Implement proper access control mechanisms to restrict unauthorized access to IoT systems.
Implementing proper access control mechanisms is crucial to safeguarding IoT systems from unauthorized access. By establishing stringent authentication and authorisation protocols, organisations can ensure that only authorised individuals have the ability to interact with IoT devices and data. This not only protects sensitive information and privacy but also helps prevent potential security breaches and cyber attacks. Prioritising access control in IoT applications is essential for maintaining the integrity and security of connected systems in today’s interconnected digital landscape.
Use encryption techniques to secure communication between IoT devices and servers.
It is crucial to utilise encryption techniques to ensure the secure communication between IoT devices and servers. By encrypting the data transmitted between these devices, we can protect sensitive information from potential cyber threats and ensure the privacy and integrity of the communication. Encryption plays a vital role in safeguarding IoT applications against unauthorized access and data breaches, ultimately enhancing the overall security posture of the interconnected system.
Monitor IoT device performance and behaviour for any anomalies that may indicate security breaches.
It is crucial to monitor the performance and behaviour of IoT devices for any anomalies that could signal potential security breaches. By closely observing the activity of these devices, we can detect unusual patterns or behaviours that may indicate a security threat. Proactive monitoring allows us to identify and address security vulnerabilities promptly, ensuring the integrity and safety of our IoT systems and data.
Consider the privacy implications of collecting and processing data from IoT devices.
When exploring IoT applications, it is crucial to consider the privacy implications of collecting and processing data from IoT devices. As these devices gather and transmit vast amounts of personal information, there is a need to ensure that robust security measures are in place to protect this data from potential breaches or misuse. It is essential for users and organisations to be mindful of the privacy risks associated with IoT technology and to implement stringent data protection practices to safeguard sensitive information effectively. By prioritising privacy considerations in the development and deployment of IoT applications, we can foster trust among users and uphold ethical standards in the digital age.
Ensure interoperability of different IoT devices by following industry standards and protocols.
Ensuring interoperability of different IoT devices is crucial for seamless communication and integration within a network. By adhering to industry standards and protocols, such as MQTT or CoAP, IoT devices can effectively exchange data and commands regardless of their manufacturer or type. This not only enhances the overall efficiency and reliability of IoT systems but also facilitates scalability and future-proofing for evolving technological requirements. Embracing interoperability standards is key to unlocking the full potential of IoT applications and creating a more interconnected and intelligent ecosystem.
Provide user education on how to securely use and manage IoT devices in their environment.
It is crucial to provide user education on securely using and managing IoT devices in their environment. By raising awareness about best practices for securing IoT devices, such as setting strong passwords, regularly updating firmware, and configuring privacy settings, users can greatly reduce the risk of cyber threats and protect their personal data. Educating users on the importance of cybersecurity in the context of IoT applications empowers them to take proactive measures to safeguard their devices and ensure a safer digital experience.
Have a disaster recovery plan in place to mitigate the impact of any potential IoT system failures.
It is crucial to have a well-thought-out disaster recovery plan in place to mitigate the impact of any potential IoT system failures. In the event of a system failure, having a comprehensive recovery strategy can help minimise downtime, prevent data loss, and ensure business continuity. By proactively planning for such scenarios, organisations can effectively address and resolve issues that may arise with their IoT applications, ultimately safeguarding their operations and maintaining a seamless user experience.
No Responses