Log Analysis: Unveiling Insights Hidden in Data
In today’s digital age, businesses generate an immense amount of data through various systems and applications. Amongst this vast sea of information lies a treasure trove of insights waiting to be discovered. Log analysis is the key that unlocks this treasure, providing organizations with valuable knowledge and actionable intelligence.
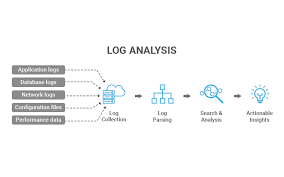
What is log analysis? It involves examining log files, which are records generated by computer systems, networks, and applications. These logs capture crucial information such as events, errors, user activities, and system performance metrics. By analysing these logs, businesses can gain a deeper understanding of their operations, identify issues or anomalies, and make informed decisions to enhance efficiency and security.
One primary application of log analysis is troubleshooting. When something goes wrong within a system or application, logs serve as a crucial source of information for diagnosing the problem. Skilled analysts can sift through the logs to identify patterns or error messages that indicate the root cause of an issue. This enables quick resolution and minimizes downtime.
Furthermore, log analysis plays a vital role in enhancing cybersecurity measures. By monitoring logs for suspicious activities or anomalies, businesses can detect potential security breaches or unauthorized access attempts. With proactive log analysis practices in place, organizations can respond swiftly to mitigate risks and protect sensitive data from falling into the wrong hands.
But log analysis isn’t just about troubleshooting and security; it also offers valuable insights for improving overall business performance. By analyzing user behavior patterns captured in logs, companies can gain deep insights into customer preferences and trends. This knowledge helps them refine marketing strategies, optimize product offerings, and provide better customer experiences.
Moreover, log analysis enables organizations to monitor system performance effectively. By tracking performance metrics recorded in logs, businesses can identify bottlenecks or inefficiencies within their infrastructure. This empowers them to optimize resource allocation, enhance scalability, and ensure smooth operations even during peak demand periods.
To perform effective log analysis, businesses often rely on advanced tools and technologies. These tools help automate the process, making it easier to handle large volumes of logs and extract meaningful insights efficiently. Machine learning algorithms and artificial intelligence are increasingly being employed to analyze logs, enabling predictive analysis and anomaly detection.
In conclusion, log analysis is a powerful technique for extracting valuable insights from the vast amount of data generated by digital systems. By harnessing the potential of log analysis, businesses can troubleshoot issues promptly, enhance cybersecurity measures, optimize performance, and gain a competitive edge in today’s data-driven world. Embracing log analysis as a strategic practice empowers organizations to make informed decisions that drive success and growth.
5 Advantages of Log Analysis: Enhancing Security, Streamlining Operations, Informed Decision-Making, Simplifying Compliance, and Cutting Costs
- Increased security
- Improved operational efficiency
- More informed decision-making
- Easier compliance management
- Reduced costs
Challenges and Concerns of Log Analysis: A Comprehensive Overview
- Log analysis can be time consuming and costly to set up.
- Log analysis can be difficult to interpret due to the sheer volume of data that needs to be analysed.
- It is difficult to detect security incidents from log files without proper training and experience in log analysis.
- Log analysis requires access to detailed system information, which can present a security risk if not properly managed.
- Some organisations may struggle with the storage capacity needed for long-term log retention and analysis requirements.
- If logs are not regularly monitored, malicious activity can go unnoticed for long periods of time, leading to potential financial loss or reputational damage for the organisation involved
Increased security
Increased Security: Log Analysis as a Shield Against Threats
In the digital landscape where cyber threats lurk around every corner, organisations must remain vigilant in safeguarding their systems and data. Log analysis emerges as a powerful tool in the arsenal of cybersecurity, providing increased security by identifying potential threats and malicious activities.
Logs serve as a detailed record of system events, user activities, and network traffic. By analysing these logs, organisations can spot anomalies or suspicious patterns that may indicate unauthorized access attempts, malware infections, or other malicious activities. This proactive approach allows businesses to detect potential threats early on and take swift action to protect their systems and data.
One of the key benefits of log analysis is its ability to provide real-time monitoring. By continuously monitoring logs, organisations can identify any unusual or suspicious activities promptly. This enables them to respond quickly and effectively, minimizing the impact of potential security breaches.
Moreover, log analysis helps in identifying patterns that may be indicative of an ongoing attack or an emerging threat landscape. By studying historical log data alongside current events, analysts can spot trends or correlations that might otherwise go unnoticed. This foresight empowers organisations to proactively fortify their defences against evolving threats.
Furthermore, log analysis aids in incident response and forensic investigations. In the unfortunate event of a security breach, logs act as a valuable source of evidence for understanding what happened and how it occurred. Analysts can trace back the steps leading up to the incident by examining relevant logs, helping them identify the root cause and prevent similar incidents from happening in the future.
To fully leverage log analysis for increased security, organisations often utilise advanced security information and event management (SIEM) systems or log management tools. These tools automate log collection, aggregation, correlation, and analysis processes. They enable efficient monitoring across multiple systems and applications while providing alerts for suspicious activities based on predefined rules or machine learning algorithms.
In conclusion, log analysis serves as a crucial line of defence in today’s cybersecurity landscape. By analysing logs, organisations can identify potential threats and malicious activities, allowing them to take proactive steps to protect their systems and data. Embracing log analysis as a security practice enables businesses to stay one step ahead of cybercriminals, ensuring the safety and integrity of their digital assets.
Improved operational efficiency
Improved Operational Efficiency: Unveiling System Performance Insights through Log Analysis
Log analysis is a powerful tool that can significantly improve operational efficiency for organizations. By delving into the wealth of data captured in log files, businesses can gain valuable insights into their system performance, enabling them to better understand how their systems are being utilized and identify areas for improvement.
One of the key advantages of log analysis is its ability to provide a comprehensive view of system operations. By analysing logs, businesses can monitor various performance metrics such as response times, resource utilization, and error rates. These insights allow organizations to identify bottlenecks or inefficiencies within their infrastructure, enabling them to take proactive measures to optimize system performance.
For example, through log analysis, businesses can identify specific processes or components that are causing delays or consuming excessive resources. Armed with this knowledge, organizations can make informed decisions about resource allocation, fine-tune configurations, or implement optimizations to streamline operations. This not only improves overall efficiency but also enhances customer experiences by ensuring smooth and responsive system performance.
Additionally, log analysis helps organizations detect patterns or trends in system usage. By studying user behavior captured in logs, businesses can gain insights into how their systems are being utilized and identify areas where improvements can be made. For instance, if certain features or functionalities are rarely used by customers, organizations may choose to reallocate resources towards more popular aspects or consider redesigning the user interface to enhance usability.
Furthermore, log analysis facilitates capacity planning and scalability. By closely monitoring system performance metrics recorded in logs over time, businesses can anticipate future resource requirements based on usage patterns. This enables them to plan for growth effectively and ensure that their systems have the necessary capacity to handle increasing demands without compromising performance.
In conclusion, log analysis offers a significant advantage in improving operational efficiency for organizations. By providing insights into system performance and usage patterns, businesses can identify areas for enhancement and make informed decisions that optimize operations. Whether it’s identifying and resolving bottlenecks, fine-tuning resource allocation, or planning for scalability, log analysis empowers organizations to streamline their systems and deliver better performance to their users. Embracing log analysis as a strategic practice enables businesses to achieve improved operational efficiency and gain a competitive edge in today’s fast-paced digital landscape.
More informed decision-making
More Informed Decision-Making: Unleashing the Power of Log Analysis
In today’s fast-paced business landscape, making well-informed decisions is crucial for success. One significant advantage of log analysis is its ability to provide organizations with valuable insights into user behavior and trends. By delving into log data, businesses can gain a deeper understanding of their environment, empowering them to make smarter decisions about future investments and strategies.
Log analysis allows organizations to track and analyze user activities, preferences, and patterns. It provides a comprehensive view of how users interact with systems, applications, and websites. By examining this data, businesses can uncover valuable information about customer preferences, engagement levels, and overall satisfaction.
Understanding user behavior is invaluable when it comes to shaping future investments. By analyzing log data, organizations can identify which features or functionalities are most popular among users. This knowledge enables them to prioritize development efforts and allocate resources effectively. They can focus on enhancing the areas that resonate most with their target audience while de-prioritizing or eliminating features that receive little traction.
Log analysis also helps organizations identify emerging trends within their environment. By spotting patterns in user behavior over time, businesses can anticipate shifts in customer preferences or industry demands. Armed with this foresight, they can adapt their strategies accordingly to stay ahead of the competition and seize new opportunities.
Moreover, log analysis enables organizations to evaluate the effectiveness of marketing campaigns or product launches. By monitoring log data related to user interactions during these initiatives, businesses can measure engagement levels and conversion rates accurately. This information allows them to assess the success of their efforts objectively and make data-driven decisions for future marketing campaigns.
Additionally, log analysis plays a vital role in improving customer experiences. By understanding how users navigate through systems or websites based on log data insights, organizations can identify pain points or areas where customers may face difficulties. Armed with this knowledge, businesses can refine their user interfaces or streamline processes to enhance overall satisfaction and loyalty.
In summary, log analysis empowers organizations to make more informed decisions. By exploring log data, businesses can gain valuable insights into user behavior, preferences, and emerging trends. Armed with this knowledge, they can allocate resources effectively, adapt strategies to changing market demands, measure the success of marketing efforts accurately, and enhance customer experiences. Embracing log analysis as a strategic practice enables organizations to stay agile in a dynamic business landscape and make decisions that drive growth and success.
Easier compliance management
Easier Compliance Management: Unveiling Regulatory Visibility through Log Analysis
In an increasingly regulated business landscape, compliance management has become a critical aspect for organizations across industries. Failure to meet regulatory requirements can result in severe consequences, including financial penalties and damage to reputation. Log analysis emerges as a valuable tool in this regard, offering enhanced visibility into an organization’s activities and facilitating easier compliance management.
One of the key advantages of log analysis is its ability to provide a comprehensive view of the activities taking place within an organization’s environment. Logs capture detailed information about user actions, system events, and application activities. By analyzing these logs, businesses can gain valuable insights into how their systems are being used and whether they comply with relevant regulations.
For example, in industries such as finance or healthcare, where data privacy is of utmost importance, log analysis can help ensure compliance with regulations like GDPR or HIPAA. By examining logs for any unauthorized access attempts or breaches, organizations can identify and mitigate potential security risks promptly. This proactive approach not only helps protect sensitive data but also demonstrates a commitment to regulatory compliance.
Furthermore, log analysis enables organizations to track and monitor user activities within their systems. This visibility allows businesses to ensure that employees are adhering to established policies and procedures. For instance, if there are specific guidelines regarding the use of company resources or access privileges, log analysis can reveal any violations or deviations from these rules. This insight enables timely intervention and corrective action if necessary.
Log analysis also aids in maintaining audit trails—a crucial component of compliance management. Logs serve as a reliable source of evidence that can be used during audits or investigations. By analyzing logs related to specific events or transactions, organizations can demonstrate their adherence to regulatory requirements and provide auditors with the necessary documentation.
Moreover, log analysis helps organizations proactively identify potential compliance gaps and address them before they escalate into serious issues. By regularly monitoring logs for patterns or anomalies that may indicate non-compliance, businesses can take preventive measures and implement necessary controls to ensure ongoing adherence to regulations.
In summary, log analysis plays a vital role in easing compliance management for organizations. By providing visibility into activities within an environment, it enables businesses to ensure regulatory compliance, protect sensitive data, and maintain audit trails. With log analysis as a strategic practice, organizations can navigate the complex landscape of regulations with confidence, mitigating risks and safeguarding their reputation.
Reduced costs
Reduced Costs: Unlocking Savings with Log Analysis
In today’s fast-paced digital landscape, businesses rely heavily on their systems and applications to keep operations running smoothly. However, system outages or malicious activities can lead to costly repairs and significant downtime. This is where log analysis proves its worth by helping organizations identify potential issues proactively, ultimately reducing costs.
By harnessing the power of log analysis, businesses gain the ability to monitor and analyze their system logs in real-time. This enables them to detect anomalies or warning signs that could indicate a potential problem before it escalates into a full-blown crisis. By identifying these issues early on, organizations can take proactive measures to address them promptly, minimizing the impact on their operations.
One of the significant cost-saving benefits of log analysis is its ability to prevent expensive repairs. By continuously monitoring system logs, businesses can identify patterns or error messages that point towards underlying issues within their infrastructure. Addressing these issues in their early stages helps prevent them from developing into more severe problems that require extensive repairs or even complete system overhauls.
Moreover, log analysis plays a crucial role in mitigating the financial impact of downtime caused by system outages. By monitoring logs for potential warning signs and promptly addressing any identified issues, organizations can significantly reduce the risk of unexpected downtime. This translates into uninterrupted operations and avoids the associated costs of lost productivity, missed opportunities, and dissatisfied customers.
Log analysis also aids in combating malicious activities such as cyberattacks or unauthorized access attempts. By closely monitoring logs for suspicious activities or anomalies, businesses can detect potential security breaches early on. This allows them to take immediate action to mitigate risks and prevent costly data breaches or damage to their reputation.
In addition to preventing costly repairs and minimizing downtime, log analysis contributes to overall cost reduction through improved resource allocation. By analyzing performance metrics recorded in logs, organizations can identify areas where resources are underutilized or overburdened. This insight enables them to optimize resource allocation, ensuring that resources are utilized efficiently and effectively. As a result, businesses can avoid unnecessary investments in additional infrastructure or equipment, leading to significant cost savings.
In conclusion, log analysis provides organizations with a powerful tool to reduce costs by identifying potential issues proactively. By leveraging real-time monitoring and analysis of system logs, businesses can prevent expensive repairs, minimize downtime, and optimize resource allocation. Embracing log analysis as a cost-saving practice allows organizations to allocate their resources more efficiently and effectively while maintaining uninterrupted operations and safeguarding against security threats.
Log analysis can be time consuming and costly to set up.
Log Analysis: The Time and Cost Conundrum
While log analysis offers a plethora of benefits for businesses, it is important to acknowledge that there are some challenges associated with this practice. One significant drawback is the time-consuming nature and the potential costs involved in setting up a robust log analysis system.
Implementing an effective log analysis system requires careful planning, resource allocation, and technical expertise. It involves collecting, aggregating, and storing logs from various sources, setting up the infrastructure to process and analyze these logs, and configuring monitoring tools to track relevant metrics. This process can be time-consuming and complex, especially for organizations with large-scale systems or distributed environments.
Moreover, the cost implications of log analysis should not be overlooked. Investing in the necessary hardware, software tools, storage solutions, and skilled personnel can incur substantial upfront expenses. Additionally, ongoing maintenance and upgrades may be required to ensure the system remains efficient and up-to-date.
Furthermore, log analysis often generates a vast amount of data that needs to be stored securely for future reference or compliance purposes. This necessitates investing in adequate storage capacity or cloud solutions that can accommodate the growing volume of logs over time. These storage costs can add up significantly over the long term.
Another aspect contributing to the complexity is the need for skilled analysts who possess expertise in log analysis techniques and tools. Hiring or training individuals proficient in log analysis can be an additional expense for organizations. Skilled analysts are essential for effectively interpreting log data, identifying patterns or anomalies, and extracting meaningful insights that drive actionable decisions.
Despite these challenges, it is important to note that advancements in technology have made log analysis more accessible than ever before. There are now numerous cost-effective solutions available in the market that cater to businesses of all sizes. Cloud-based log management platforms have emerged as a popular choice as they offer scalability and reduced infrastructure costs.
Additionally, organizations can leverage open-source tools or frameworks to minimize upfront expenses associated with commercial software licenses. These tools provide a foundation for building a tailored log analysis system that meets specific business requirements.
While log analysis may require an initial investment of time and resources, the benefits it brings in terms of troubleshooting, security, performance optimization, and business insights often outweigh the associated costs. It is crucial for organizations to carefully evaluate their needs, consider available options, and strike a balance between the costs and the potential value derived from log analysis.
In conclusion, while log analysis can be time-consuming and costly to set up initially, the long-term benefits it offers make it a worthwhile investment for businesses. By carefully considering available solutions, leveraging technology advancements, and allocating resources effectively, organizations can overcome these challenges and unlock the hidden value within their log data.
Log analysis can be difficult to interpret due to the sheer volume of data that needs to be analysed.
The Challenge of Log Analysis: Overcoming the Deluge of Data
Log analysis is undoubtedly a powerful tool for extracting insights and improving business operations. However, like any analytical process, it comes with its own set of challenges. One significant hurdle that analysts often face is the overwhelming volume of data that needs to be analyzed.
In today’s digital landscape, organizations generate an enormous amount of log data from various sources such as servers, networks, applications, and security systems. These logs capture a multitude of events, errors, and user activities, creating a vast pool of information to sift through. As a result, interpreting this sheer volume of data can be a daunting task.
The first challenge lies in managing and processing this massive amount of log data efficiently. Traditional manual analysis methods are simply not feasible when dealing with such extensive datasets. Analysts can easily find themselves drowning in a sea of log files, struggling to identify relevant patterns or anomalies amidst the noise.
Another obstacle is the complexity and diversity of log formats. Different systems and applications generate logs in their unique formats, making it difficult to consolidate and analyze them effectively. This requires analysts to invest time in understanding the intricacies of each log format or employ specialized tools that can handle multiple formats.
Moreover, the dynamic nature of log data further complicates the analysis process. Logs continuously stream in real-time, making it challenging for analysts to keep up with the influx while simultaneously analyzing historical data. The need for near real-time analysis adds an additional layer of complexity to ensure timely detection and response to critical events.
To overcome these challenges, organizations are turning towards advanced technologies and solutions that automate the log analysis process. Machine learning algorithms and artificial intelligence can help streamline log analysis by automatically identifying patterns or anomalies within massive datasets. These intelligent tools assist analysts in focusing their efforts on interpreting meaningful insights rather than getting lost in the sea of raw data.
Furthermore, implementing effective log management strategies is crucial for successful log analysis. This includes proper log collection, storage, and retention policies. By organizing logs in a structured manner and implementing efficient log management practices, organizations can significantly simplify the analysis process.
In conclusion, while log analysis offers valuable insights, the sheer volume of data involved can present challenges. However, with the right tools, technologies, and strategies in place, organizations can overcome these hurdles and unlock the hidden potential within their log data. By streamlining the analysis process and focusing on meaningful insights, businesses can leverage log analysis to drive improvements and make informed decisions that propel them towards success.
It is difficult to detect security incidents from log files without proper training and experience in log analysis.
The Challenge of Log Analysis: Detecting Security Incidents Requires Expertise
Log analysis is a valuable practice that offers numerous benefits to businesses, but it does come with its own set of challenges. One significant challenge is the difficulty of detecting security incidents from log files without proper training and experience in log analysis.
In today’s complex digital landscape, cyber threats are constantly evolving, making it crucial for organizations to have robust security measures in place. Log files serve as a valuable source of information for identifying potential security breaches or unauthorized access attempts. However, effectively detecting these incidents requires more than just access to log data; it demands expertise in interpreting and analyzing the logs.
Without proper training and experience in log analysis, security incidents can easily go unnoticed. Log files are often voluminous and contain a vast amount of information that may seem overwhelming to the untrained eye. Skilled analysts possess the knowledge and techniques necessary to identify patterns, anomalies, or suspicious activities within these logs.
Moreover, log files may contain cryptic error messages or complex event sequences that require a deep understanding of system architectures and network protocols to decipher. Without this expertise, it becomes challenging to differentiate normal system behavior from potentially malicious activities.
Additionally, as cyber threats become increasingly sophisticated, attackers often employ techniques designed to evade detection. They may intentionally manipulate logs or use encryption methods that make it difficult for traditional log analysis techniques to uncover their activities. Skilled analysts with specialized training can employ advanced methodologies and tools to overcome these challenges and detect such hidden threats.
To address this con of log analysis effectively, organizations should invest in training their cybersecurity teams or consider partnering with experts who specialize in log analysis. By equipping analysts with the necessary skills and knowledge, businesses can enhance their ability to detect security incidents promptly and respond appropriately.
Furthermore, leveraging advanced technologies such as machine learning algorithms and artificial intelligence can augment the capabilities of log analysis tools. These technologies can assist analysts in automating certain aspects of log analysis, reducing the manual effort required and enabling more efficient detection of security incidents.
In conclusion, while log analysis is a powerful tool for identifying security incidents, it does require proper training and experience to be effective. Organizations must acknowledge the complexity of log analysis and invest in developing the expertise necessary to detect and respond to potential threats. By doing so, they can strengthen their cybersecurity posture and safeguard their digital assets from evolving cyber threats.
Log analysis requires access to detailed system information, which can present a security risk if not properly managed.
The Con of Log Analysis: Balancing Access and Security
Log analysis is undoubtedly a powerful tool for businesses to gain valuable insights from their data. However, like any other technology, it comes with certain challenges that need to be addressed. One such concern is the potential security risk associated with accessing detailed system information.
To perform effective log analysis, analysts require access to comprehensive and detailed logs that capture various events and activities within a system or application. This level of access provides them with the necessary information to identify issues, troubleshoot problems, and make informed decisions.
However, granting such access to log files can also present a security risk if not properly managed. Detailed system information may contain sensitive data, including user credentials, IP addresses, or proprietary business information. If this data falls into the wrong hands or is accessed by unauthorized individuals, it can lead to severe consequences such as data breaches or insider threats.
To mitigate this risk, organizations must implement robust security measures when handling log files. Here are some best practices to consider:
- Access Control: Implement strict access control mechanisms to ensure that only authorized personnel can view and analyze log files. This includes role-based access controls (RBAC), multi-factor authentication (MFA), and regular review of user privileges.
- Encryption: Encrypt log files both at rest and in transit to protect the sensitive information they contain. This ensures that even if logs are intercepted or accessed unlawfully, the data remains unreadable without proper decryption keys.
- Secure Storage: Store log files in secure environments with restricted physical and logical access controls. This prevents unauthorized individuals from physically tampering with or copying sensitive logs.
- Monitoring and Auditing: Implement real-time monitoring and auditing mechanisms to track who accesses log files and detect any suspicious activities promptly. Regularly reviewing audit logs helps identify any potential security breaches or unauthorized access attempts.
- Anonymization/Redaction: Consider anonymizing or redacting sensitive information within log files before granting access to analysts. This ensures that personally identifiable information (PII) or other sensitive data is not exposed during log analysis.
By implementing these security measures, organizations can strike a balance between gaining valuable insights through log analysis and protecting the confidentiality, integrity, and availability of their systems and data.
In conclusion, while log analysis offers tremendous benefits, organizations must be mindful of the security risks associated with accessing detailed system information. By implementing robust security measures and adhering to best practices, businesses can mitigate these risks and harness the power of log analysis without compromising data security. Striking this balance is crucial for maintaining trust, safeguarding sensitive information, and ensuring the success of log analysis initiatives.
Some organisations may struggle with the storage capacity needed for long-term log retention and analysis requirements.
The Storage Challenge: A Con of Log Analysis
While log analysis offers numerous benefits to organizations, it is important to acknowledge that it also comes with its own set of challenges. One significant con that some organizations may face is the struggle with storage capacity needed for long-term log retention and analysis requirements.
Logs generated by computer systems, networks, and applications can accumulate rapidly over time. As businesses grow and their operations expand, the volume of logs increases exponentially. Storing these logs for an extended period becomes a daunting task, especially considering the need for compliance with industry regulations or legal requirements.
Long-term log retention is crucial for several reasons. It allows organizations to maintain a historical record of events, which can be invaluable for troubleshooting past issues or conducting forensic investigations. Additionally, logs serve as an essential source of data for trend analysis and identifying patterns over time.
However, storing large volumes of logs requires significant storage capacity. Traditional storage solutions may not be able to handle the scale and complexity of log data efficiently. This can lead to increased costs associated with acquiring and maintaining additional storage infrastructure.
Moreover, as log files continue to accumulate, searching through them becomes more time-consuming and resource-intensive. Retrieving specific information from vast amounts of stored logs can be a slow process without efficient indexing or search capabilities in place.
To address this challenge, organizations have several options available. They can invest in scalable storage solutions that can accommodate the growing volume of log data effectively. Cloud-based storage services offer flexibility and scalability without the need for extensive on-premises infrastructure.
Another approach is implementing log rotation policies that prioritize relevant logs while archiving or discarding less critical ones. This helps reduce the overall storage burden while still retaining essential information for analysis purposes.
Organizations can also consider implementing data compression techniques to optimize storage utilization without compromising data integrity or accessibility. Compressed logs take up less space while still retaining their original content and value.
Furthermore, employing log management and analysis tools that provide efficient indexing and search functionalities can significantly enhance the process of retrieving specific information from stored logs. These tools help organizations navigate through vast amounts of log data swiftly, saving time and resources.
In conclusion, while log analysis brings valuable insights to organizations, the storage challenge associated with long-term log retention and analysis requirements cannot be ignored. However, with careful planning, investment in scalable storage solutions, and the adoption of efficient log management tools, organizations can overcome this con and leverage the benefits of log analysis without compromising on data retention or accessibility.
If logs are not regularly monitored, malicious activity can go unnoticed for long periods of time, leading to potential financial loss or reputational damage for the organisation involved
The Hidden Danger: The Con of Neglected Log Analysis
Log analysis is a powerful tool that provides valuable insights into system performance, user behavior, and security. However, like any other tool, it has its limitations and potential pitfalls. One significant con of log analysis arises when logs are not regularly monitored, leading to the risk of malicious activity going unnoticed for extended periods. This can result in severe financial loss and reputational damage for the organization involved.
Logs serve as a digital footprint of activities within a system or application. They capture events, errors, and user actions that occur over time. When logs are diligently monitored, organizations can detect anomalies or signs of malicious activity promptly. Suspicious patterns or unauthorized access attempts can be identified and addressed before they cause significant harm.
However, neglecting log analysis leaves organizations vulnerable to undetected threats. Malicious actors often exploit this oversight by infiltrating systems and remaining undetected for extended periods. They may quietly exfiltrate sensitive data or manipulate systems to their advantage without triggering any alarms.
The consequences of such negligence can be severe. Financial loss may occur through data breaches or unauthorized access to financial accounts. Intellectual property theft could result in competitive disadvantages or loss of trade secrets. Additionally, reputational damage is a significant concern as customers lose trust in an organization’s ability to protect their data and privacy.
To mitigate this con of log analysis, organizations must prioritize regular monitoring and analysis of logs. Implementing robust log management practices ensures that logs are consistently reviewed for any suspicious activities or abnormal patterns. This proactive approach allows businesses to identify potential threats early on and take appropriate measures to mitigate risks effectively.
Automated log monitoring solutions can assist in this process by continuously analyzing logs in real-time for signs of malicious activity. These tools can flag unusual events or trigger alerts based on predefined rules or machine learning algorithms that learn from historical data.
Furthermore, organizations should establish incident response protocols to swiftly address any identified threats. A well-defined incident response plan ensures that appropriate actions are taken promptly, minimizing the potential damage caused by undetected malicious activity.
In conclusion, neglecting regular log analysis poses a significant risk to organizations. Failing to monitor logs diligently allows malicious activity to go unnoticed for extended periods, potentially leading to financial loss and reputational damage. By prioritizing regular log monitoring and implementing robust incident response protocols, businesses can mitigate this con and safeguard their systems, data, and reputation from the hidden dangers of neglected log analysis.
No Responses